Introduction
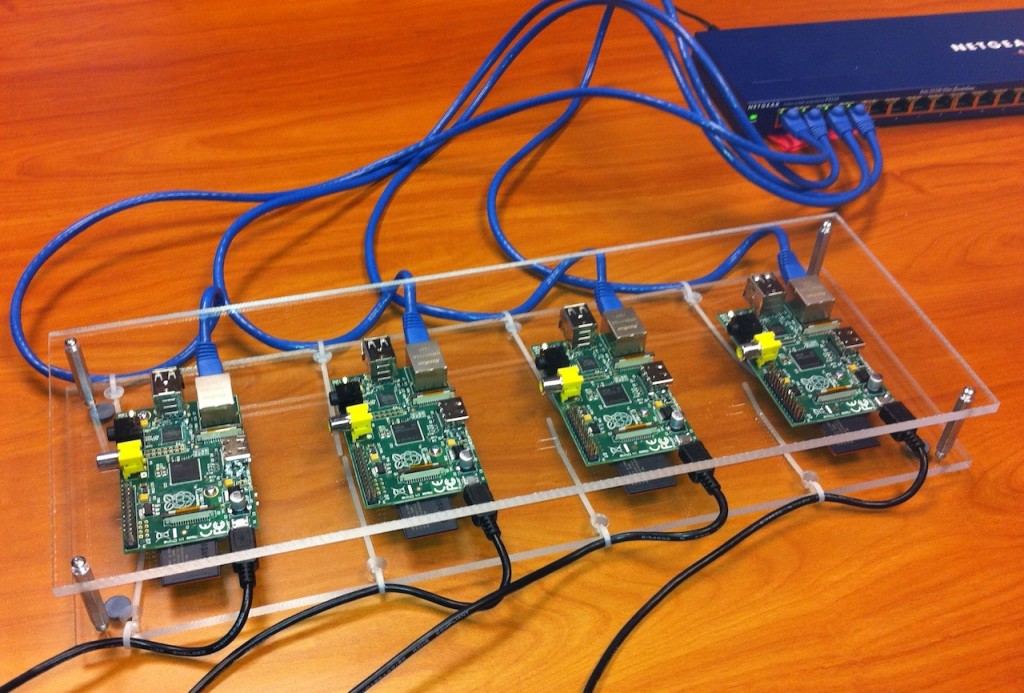
Actually Raspberry Pi is a low performance computer board, however, we can use cluster technology to build of a powerful Raspberry Pi computer by combining several pi. It is very scalable. We can use “Riak” software to build the cluster function on Raspberry Pi. It can improve the data process power to speed-up the data upload and download process. I will introduce the installation of Riak in the following.
Step 1 Prerequisite Requirement – Installation of mysql & esl-erlang
1.0 Install mysql by running the following command:
$ sudo apt-get install mysql-server mysql-clietn php5-mysql
$ sudo apt-get install phpmyadmin
$ sudo nano /etc/apache2/apache2.conf
add the following line to the end:
Include /etc/phpmyadmin/apache.conf
1.1 Add the following line to your /etc/apt/sources.list:
deb http://binaries.erlang-solutions.com/debian wheezy contrib
(you may remove all other lines in the file)
1.2 Add erlang Key:
$ cd ~$ sudo wget –o – http://binaries.erlang_solutions.com/debian/erlang_solutions.asc | sudo apt-key add –
1.3 Installation of esl-erlang
$ sudo apt-get update
$ sudo apt-get install esl-erlang
$ sudo reboot
Tips: If you have problem to install esl-erlang, you can try to install erlang-mini.
Step 2: Download the riak-1.2.1 version from the web site
http://s3.amazonaws.com/downloads.basho.com/riak/1.2/1,2.1/riak-1.2.1.tar.gz
$ tar zxvf riak-1.2.1.tar.gz$ mv riak-1.2.1 ~
$ cd ~/riak-1.2.1
Tips: I tried the latest version, but could not succeed to install; so I referred to use version 1.2.1)
Step 3: Installation of Riak
$ sudo make
$ sudo make rel
Tips: If you meet error message “Unable to generate spec: read file info /usr/lib/erlang/man/man3/cerfcl.3.gzfailed make: *** [generate] Error 1”, you can remove those cert* files to solve the problem as below, and then re-run “sudo make rel” command :
$ sudo mv /usr/lib/erlang/man/man3/cerfcl.3.gz ~
$ sudo mv /usr/lib/erlang/man/man3/cerfl.3.gz ~
$ sudo mv /usr/lib/erlang/man/man3/cerff.3.gz ~
$ sudo mv /usr/lib/erlang/man/man3/cerfcf.3.gz ~
Step 4: Test Riak
4.1. start Riak process
$ cd ./rel/riak$ sudo ./bin/riak start
4.2 Test Riak process
4.2.1 First Test:
pi@gopi1:~/riak-1.2.1/rel/riak/bin $ curl http://192.168.5.78:8098/ping
OKpi@gopi1:~/riak-1.2.1/rel/riak/bin $
You will see OK display after run curl command as red highlight above.
4.2.2 Second Test on Speed:
pi@gopi1:~/riak-1.2.1/rel/riak/bin $ curl http://192.168.5.78:8098/riak/druple?keys=true | json_pp
% Total % Received % Xferd Average Speed Time Time Time Current
Dload Upload Total Spent Left Speed
100 436 100 436 0 0 1153 0 –:–:– –:–:– –:–:– 1159
{
“keys” : [],
“props” : {
“young_vclock” : 20,
“postcommit” : [],
“dw” : “quorum”,
“basic_quorum” : false,
“allow_mult” : false,
“w” : “quorum”,
“linkfun” : {
“mod” : “riak_kv_wm_link_walker”,
“fun” : “mapreduce_linkfun”
},
“name” : “druplets”,
“notfound_ok” : true,
“chash_keyfun” : {
“fun” : “chash_std_keyfun”,
“mod” : “riak_core_util”
},
“pr” : 0,
“old_vclock” : 86400,
“last_write_wins” : false,
“big_vclock” : 50,
“rw” : “quorum”,
“pw” : 0,
“precommit” : [],
“small_vclock” : 50,
“r” : “quorum”,
“n_val” : 3
}
}
Step 5: Setup Cluster on Two Raspberry Pi
5.1. Ensure a static ip address was setup in /etc/network/interfaces
5.2. edit ~/riak-1.2.1/rel/riak/etc/vm.args file by changing the following line to assign ip as:
-name riak@127.0.0.1 –> -name riak@192.168.5.78
5.3. edit ~/riak-1.2.1/rel/riak/etc/app.config file by changing the following lines to assign ip as:
{pb_ip, “127.0.0.1” }, –> {pb_ip, “192.168.5.78” },
{http, [ {“127.0.0.1”, 8098 } ]}, –> {http, [ {“192.168.5.78”, 8098 } ]},
%{https, [{ “127.0.0.1”, 8098 }]}, –> %{https, [{ “192.168.5.78”, 8098 }]},
Do the 5.1, 5.2, and 5.3 for other Raspberry Pi, for example, setup another pi with ip 192.168.5.88.
5.4. Start the Riak in all Raspberry Pi by the following command: ~/riak-1.2.1/rel/riak/bin $ sudo ./riak start
5.5 Setup Cluster Process by adding salve to master, by running the command in master raspberry pi:
~/riak-1.2.1/rel/riak/bin $ sudo ./riak-admin cluster join riak@192.168.5.88
5.6 Test Cluster Process
pi@gopi1:~/riak-1.2.1/rel/riak/bin $ sudo ./riak-admin member-status
================================= Membership ==================================
Status Ring Pending Node
——————————————————————————-
joining 0.0% — ‘riak@192.168.5.88’
valid 100.0% — ‘riak@192.168.5.78’
——————————————————————————-
Valid:1 / Leaving:0 / Exiting:0 / Joining:1 / Down:0
Will Change to below after success:
——————————————————————————-
valid 50.0% — ‘riak@192.168.5.78’
valid 50.0% — ‘riak@192.168.5.88’
——————————————————————————-
Valid:2 / Leaving:0 / Exiting:0 / Joining:0 / Down:0
5.7 Check the Process Speed:
pi@gopi1:~/riak-1.2.1/rel/riak/bin $ curl http://192.168.5.78:8098/riak/druplets?keys=true | json_pp
% Total % Received % Xferd Average Speed Time Time Time Current
Dload Upload Total Spent Left Speed
100 436 100 436 0 0 5119 0 –:–:– –:–:– –:–:– 5190
{
“keys” : [],
“props” : {
“name” : “druplets”,
“chash_keyfun” : {
“mod” : “riak_core_util”,
“fun” : “chash_std_keyfun”
},
“postcommit” : [],
“big_vclock” : 50,
“small_vclock” : 50,
“allow_mult” : false,
“linkfun” : {
“mod” : “riak_kv_wm_link_walker”,
“fun” : “mapreduce_linkfun”
},
“last_write_wins” : false,
“old_vclock” : 86400,
“precommit” : [],
“r” : “quorum”,
“w” : “quorum”,
“basic_quorum” : false,
“pr” : 0,
“pw” : 0,
“rw” : “quorum”,
“young_vclock” : 20,
“n_val” : 3,
“notfound_ok” : true,
“dw” : “quorum”
}
}
Bonus:
You can install “Siege” Software to test the web speed performance, and its installation procedure is as below:
sudo apt-get install siege
(If cannot auto-install, try the following manual-install)
Download from https://www.joedog.org/2015/11/siege-3.1.3/
tar xvf siege-3.1.3.tar.gz
cd siege-3.1.3
sudo ./configure
sudo make
sudo make install
sudo make uninstall
(Testing as below command)
siege –c200 –d1 –r1 –v http://localhost/index.html