最近兩個月,我公司的電郵系統地址經常被 http://www.spamhaus.org/ 列到 CBL 黑名單中,而限制了電郵的傳送,影響公司運作。CBL 黑名單的起因是網絡內某些電腦中了木馬病毒,例如:Conficker botnet,這會发送了大量的垃圾邮件给对方,因而被封鎖。我用過網絡掃描、更新殺毒軟件…等等方法,解決了問題,但是,一、兩星期後,又再被列到CBL 黑名单中,經常解決後又發生,是認真煩擾。
剛好收到雲盟公司郵件中繼轉發服務的廣告,此服務主要解決的是外發郵件退回問題,企業郵件服務器通過設置中繼轉發服務器地址,便可保證正常發送;而服務價錢不貴,唯有採用吧。
唉!我真懷疑制造問題和解決問題的是同一火伙人,我們越是倚賴某事,便越大機會被人利用來威脅,詐取好處,例如這次的電郵問題;所以最好便是充實自己,有能力自保,不受威脅。
>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>
參考資料:
3. http://www.spamhaus.org/lookup.lasso
4. How to find BOTs in a LAN
4.1 On Windows, use this in a dos command window:
在DOS 下跑 : netstat 5
This will give you a list of all network connections your machine has open, much like *NIX netstat above every 5 seconds until you stop it. You’re looking for very much the same sort of things as *NIX netstat above. You’ll probably see Microsoft, Yahoo and other familiar names – they’re normal (from your browser, IM etc). “Akamai” perhaps won’t be familiar, but it’s normal too. Lots of port 25 connections is the usual sign of infection.
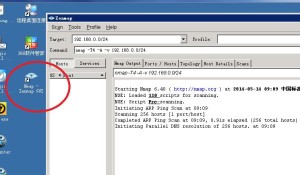
4.2 Port Scanners using Nmap tool
Detailed description of how to use nmap is well beyond the scope of this paper. For our purposes, the following command will do most of what you want and be non-destructive – won’t do any damage:
nmap -A [machine or network specification]