Introduction
 Raspberry Pi is a low cost, high power and small size Linux Server or Computer. I foresee that it will become very popular in future, especially using in automatic controller aspect which is the next generation of computer world. An important topic for setup a raspberry pi server is about server hardening, which we have better setup a security server before explore it to www. I will introduce you the step by step security setup of Raspberry Pi which is installed with NOOBS O/S in the following.
Raspberry Pi is a low cost, high power and small size Linux Server or Computer. I foresee that it will become very popular in future, especially using in automatic controller aspect which is the next generation of computer world. An important topic for setup a raspberry pi server is about server hardening, which we have better setup a security server before explore it to www. I will introduce you the step by step security setup of Raspberry Pi which is installed with NOOBS O/S in the following.
1. Initialize Setup Right After Installed NOOBS
Run the following command when first time successfully install and startup the NOOBS O/S:
raspi-config
Then, navigate the menu with the arrow keys, select things by pressing the enter key. Do the following:
- Change the Pi password
We’ll be deleting the default “pi” user account later (for security) but right now, if you were connected to the internet your Pi would be susceptible to someone SSHing into it – because every Pi has the same default password. Better to change it now, before you’re connected, just in case. - Disable “Boot to Desktop”
Currently that means entering the “Enable boot to desktop” menu item and then selecting “no”. We won’t be using the desktop (we’re going to run headless), and disabling the boot to desktop option will free up some system resources so the Pi performs better. - Update your Locale settings
If you’re in the UK then it’s already set to use UK English in UTF8 – if not, pick the best choice for your location and if you can, a UTF-8 version of your locale. Also set your timezone (for me that’s Europe > London). - Set your Hostname (Advanced > Hostname).
Your ‘hostname’ is simply the name of the Pi itself, you can choose anything but don’t use special characters or spaces. So, for example, ‘webserver1′ might be good for you. - Set the Memory Split (Advanced > Memory Split).
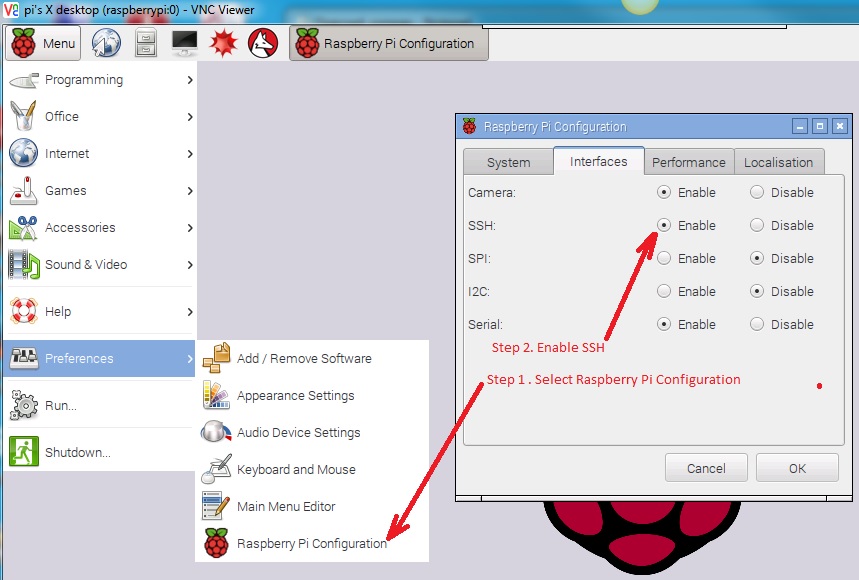
The Pi’s GPU and CPU both share the same RAM modules (512Mb of it in current Pi models). As we won’t be running a desktop we don’t need the GPU to have much memory, so we can set it to 16 – leaving the rest of the RAM free for the system to use. - Ensure SSH is enabled (Advanced > SSH).
SSH is the protocol we will be using to access and control the Pi from another computer. It must be enabled for us to do that. - Commit the changes and reboot
Select ‘Finish’ – if it asks, yes you want to reboot. If it doesn’t ask to reboot then force a reboot so the new hostname and other changes take effect; type:
$ sudo reboot
Once it’s rebooted you’ll be prompted for the username/password. Use ‘pi’ and the password you just set up.
2. Security of User/Group Setup
Step 1. Creating a new user
To get rid of the default ‘pi’ user to make it harder for anyone. Firstly, we need to create a new user by typing the command with replacing your own username as USERNAME in the following:
$ sudo useradd -m -G adm,dialout,cdrom,sudo,audio,video,plugdev,games,users,netdev,input USERNAME
Next we set a password for the new user:
$ sudo passwd USERNAME
Complete the prompts as they appear. Now shutdown the Pi:
$ sudo shutdown -h now
The Pi will turn itself off. Un-plug the power, plug in the network cable, then plug the power back in. The Pi will boot up and leave you in a Bash shell asking for a login name: Log-in with your newly created user’s details (i.e., don’t log in as ‘pi’).
Step 2. Deleting the default ‘pi’ user (optional: as long as you are comfortable with the newly created user above)
Type:
$ sudo deluser –remove-all-files pi
This will take a little while and spit out a lot of lines of text – eventually it will say ‘Done’. The ‘pi’ user and it’s associated files are now removed from the system.
3. Updating the operating system and software
Connect to internet and update the system:
$ sudo apt-get update
Wait for this to complete; it’s just got a list of all the potential updates and new bits of software you could install. To upgrade all of the currently installed software type:
$ sudo apt-get upgrade
Wait for that to complete, answer any prompts with ‘y’ + Enter. Your system is now up-to-date.
4. Fixing your machine’s internal IP address
The default network ip address is using DHCP. If you are familiar with network address setup, you can change and setup from DHCP to STATIC type; otherwise, I advise you not change it, however, I suggest you bind the MAC address of Raspberry Pi to the router in order to get a fix ip address from the router all the time
- Find the MAC address of the Pi
- Set the router to always assign the same IP to any device with that MAC address.
Note: A MAC address is a unique identifier – any and all devices attached to your network have their own unique MAC address – think of it like a serial number; no other Pi (or other device) shares the same MAC address as yours. To find your Pi’s MAC address in detail, type the following command:
$ ifconfig
5. Securing Pi Connection with SSH
Using SSH key-pair authentication is more secure than typing a password to authenticate your user (i.e., to log-in to your Pi).
From Client Side, you can download puTTY and use it to connect to Pi via SSH, or type the following SSH command:
> ssh USERNAME@IPADDRESS
6. Securing Pi with Fail2Ban
This application helps to prevent hacking attempts by detecting log-in attempts that use a dictionary attack and banning the offending IP address for a short while. NOTE: If you’re using SSH Key Pairs and have disabled SSH Password Authentication then you may not want to bother with this as no-one can hack their way in via a dictionary attack anyway.
$ sudo apt-get install fail2ban
Wait for this to complete; it should be fine running the default set up so you can stop there, or learn more about customising fail2ban.
7. SSL Setup on Apache
7.1 Create a 3 years life (1095 days) SSL certification file under directory /etc/apache2/ssl with following command:
$ sudo mkdir /etc/apache2/ssl
$ sudo openssl req -x509 -nodes -days 1095 -newkey rsa:2048 -out /etc/apache2/ssl/server.crt -keyout /etc/apache2/ssl/server.key
You need to answer some question as below example:
pi@raspberrypi:~ $ sudo openssl req -x509 -nodes -days 1095 -newkey rsa:2048 -out /etc/apache2/ssl/server.crt -keyout /etc/apache2/ssl/server.key
Generating a 2048 bit RSA private key
……………………………………………………………………………………….+++
……………………………………+++
writing new private key to ‘/etc/apache2/ssl/server.key’
—–
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter ‘.’, the field will be left blank.
—–
Country Name (2 letter code) [AU]:HK
State or Province Name (full name) [Some-State]:HK
Locality Name (eg, city) []:HK
Organization Name (eg, company) [Internet Widgits Pty Ltd]:Gold
Organizational Unit Name (eg, section) []:IT
Common Name (e.g. server FQDN or YOUR name) []:YourDomainName.com
Email Address []:youremail@hotmail.com
Remark: It is important to setup the Common Name, which should match your internet domain name FQDN.
7.2 Install the SSL mod for apache with command sudo a2enmod ssl as below example:
pi@raspberrypi:~ $ sudo a2enmod ssl
Considering dependency setenvif for ssl:
Module setenvif already enabled
Considering dependency mime for ssl:
Module mime already enabled
Considering dependency socache_shmcb for ssl:
Module socache_shmcb already enabled
Module ssl already enabled
7.3 Check the default-ssl.conf configure file under /etc/apache2/sites-enabled directory as below:
pi@raspberrypi: /etc/apache2/sites-enabled $ ls -l
total 0
lrwxrwxrwx 1 root root 35 Dec 18 22:21 000-default.conf -> ../sites-available/000-default.conf
lrwxrwxrwx 1 root root 35 Dec 18 23:11 default-ssl.conf -> ../sites-available/default-ssl.conf
If you cannot find the default-ssl.conf file in this directory, you need to run the following command to create link:
$ sudo ln -s /etc/apache2/sites-available/default-ssl.conf /etc/apache2/sites-enabled/default-ssl.conf
7.4 Edit the default-ssl.conf file and change two lines as below:
$ sudo nano /etc/apache2/sites-enabled/default-ssl.conf
SSLCertificateFile /etc/apache2/ssl/server.crt
SSLCertificateKeyFile /etc/apache2/ssl/server.key
7.5 Restart the apache server as below example:
pi@raspberrypi:/etc/apache2/sites-enabled $ sudo /etc/init.d/apache2 restart
[ ok ] Restarting apache2 (via systemctl): apache2.service.
7.6 Now, you can browse the web site with web link as https://yourdomainname.com, but you need to accept the security exceptional message to browse the site. As a result, it forces the SSL encryption on each page that require authentication, and it is more safety for data transfer in internet.
Remark: If you connect to the https://yourdomainname.com through your router, you need to open the port 443 on the router in order to allow data transfer through it.
Bonus Information:
- For WordPress SSL setup, you need to edit wp-config.php file to define the following two lines:
define(‘FORCE_SSL_LOGIN’, true);
define(‘FORCE_SSL_ADMIN’, true);
- For phpmyadmin SSL setup, you need to edit its config_inc.php file to define the following line:
$cfg[‘ForceSSL’] = ‘true’;
Reference Link / Doc:
- https://mattwilcox.net/web-development/setting-up-a-secure-home-web-server-with-raspberry-pi
- https://hallard.me/enable-ssl-for-apache-server-in-5-minutes/