1. INTRODUCTION
The presence of unsecured or mis-configured modems attached to computers on the network can undermine a well thought-out security plan. Persons unaware of the risks may set up modems on their computers that can be accessed with either non password or an easily guessed password. These modems are then vulnerable to computer criminals who “war dial,” or call numbers systematically until they find a phone number that connects to an unsecured dialup.
If a computer with an unsecured modem is connected to our network, anyone with a little computer skill and malicious intent can use that unsecured modem as a “back door” into our network. Firewalls don’t protect a network against this type of attack because the intruder comes in over phone lines, rather than over the Internet, bypassing firewalls.
2. Scope
To ensure our telephone/network systems without unsafe modem, our company would perform “war dialing” to perform system audit. To select a reliable war-dialing tool, we would not to use some public available shareware written by amateur programmers, whose intent might be toll fraud, but we select to use “PhoneSweep” software, which was designed and written specifically as a security audit tool by an experienced team of engineers and security professionals.
Although scanning phone numbers, that we are not authorized to scan, is not illegal in HK, it still deviates the ethical use of PhoneSweep according to the PhoneSweep End User License Agreement. Hence, be ensure that we have a clear permission to scan the phone system numbers before perform.
3. Owner
IT-Dept.
4. PHONESWEEP OPERATION
4.1. Introduction of PhoneSweep
PhoneSweep is a program developed by Sandstorm Enterprises (http://www.sandstorm.net) to search for modems within a set of phone numbers. PhoneSweep attempts to identify systems attached to remote modems as well as attempting to find areas of poor security by guessing common usernames and passwords.
Some modems are of higher quality than others, and can report more information about a remote phone number. These modems can recognize remote fax machines, phones answered by human beings, or simply when a remote number is ringing. Sandstorm Enterprises, Inc. makes available a recommended modem list, including modems known to work well with PhoneSweep.
Without a recommended modem, PhoneSweep must rely on a time-based timeout to end a connection. It will only be able to differentiate between calls to modems, busy signals, and calls that timed out. PhoneSweep will not then include a list of fax, voice, and ring timeout numbers.
4.2. Setup of PhoneSweep
The setup of PhoneSweep is simple. PhoneSweep uses one or more modems to place calls to a specified list of phone numbers. If a call to a remote phone number is answered, PhoneSweep collects and records information about the answering device.
PhoneSweep is highly configurable and offers advanced features such as system identification, brute force username/password guessing and customizable reporting.
4.3. Operation of PhoneSweep
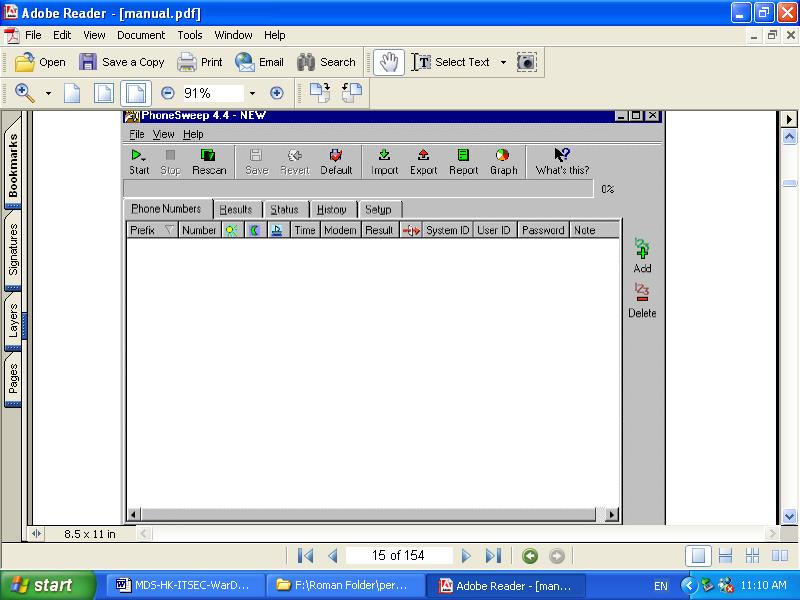
The PhoneSweep user interface is designed so that finding what you want is like looking through a card file as below.
You can refer to the on-line help from PhoneSweep software, or from the PhoneSweep user manual for the detail operation instruction.
4.4. Schedule of PhoneSweep Scanning
Our company is schedule to perform war dialling in week# 15 & 40 each year.
4.5. Roles and Responsibilities
| Role | Responsibilities |
| IT Operation Manager |
|
| IT Security Officer |
|
| IT System team |
|
5. Definition and Abbreviations
5.1. PhoneSweep Terminology
An “anomaly” is a PhoneSweep result that is not consistent and should be investigated. For instance, if a phone number is answered once with “carrier” (answered by a modem) but later answered by a human voice, this is an anomaly and may indicate an unauthorized modem.
| Term | Definition |
| Anomaly | An “anomaly” is a PhoneSweep result that is not consistent and should be investigated. For instance, if a phone number is answered once with “carrier” (answered by a modem) but later answered by a human voice, this is an anomaly and may indicate an unauthorized modem. |
| Brute force password guessing | “Brute Force” username password guessing means that PhoneSweep will call a remote number, and offer one of its assigned username/password pairs. |
| Compromised or Penetrated | A system has been “compromised” or “penetrated” if PhoneSweep was able to guess a valid username and password for that system, or the system allowed access without a username and password. |
| PhoneSweep | A program developed by Sandstorm Enterprises (www.sandstorm.net) to search for modems within a set of phone numbers. PhoneSweep can attempt to identify systems attached to remote modems as well as attempting to find areas of poor security by guessing common usernames and passwords. |
| Scan or Sweep | A PhoneSweep “scan” or “sweep” is a series of calls to a list of assigned numbers to search for modems, and possibly identify or attempt to penetrate the attached systems. |
| Username/password recycling | If PhoneSweep is “recycling” usernames and passwords, then it will attempt to brute force the entire username/password list on each modem that it finds. If it is not recycling, it will use each username/password pair on its list only once. |
5.2. Call Response States
The remote phone number responded with a carrier signal — a tone signal that indicates a computer is attached to the other end. A carrier signal means that electronic data transfer between two computers is possible, which may mean that network-based security can be evaded. Numbers with “carrier” are also referred to as numbers with modems attached. The remote phone number answered with a dial tone. “Tone” calls may indicate a number that an unauthorized person may use to make toll calls at your expense. These should be checked to make sure that they cannot be misused.
| Call response state | Explanation |
| Busy | This phone number was always busy when dialed. If a busy number is later redialed and is not busy, it is listed under the other category. |
| Carrier | The remote phone number responded with a carrier signal — a tone signal that indicates a computer is attached to the other end. A carrier signal means that electronic data transfer between two computers is possible, which may mean that network-based security can be evaded. Numbers with “carrier” are also referred to as numbers with modems attached. |
| Fax | A fax machine answered the remote phone number. |
| Ring Timeout | If your modem can detect when a remote phone number is ringing, PhoneSweep will record calls that ring past a limit as “Ring Timeout”. The ring limit varies based on the time period during which the phone number was called. |
| Screened | A phone number is “screened” if the number is “9911”, “911”, or a number added to the screened list. Screening is designed to prevent accidental calls to emergency numbers in certain countries, including the United States and Canada. |
| Timeout | PhoneSweep has timeout settings that vary depending on the time period in which the phone number was dialed. If the remote number is not ringing (or your modem cannot detect rings), and nothing answers the phone, the call times out. |
| Tone | The remote phone number answered with a dial tone. “Tone” calls may indicate a number that an unauthorized person may use to make toll calls at your expense. These should be checked to make sure that they cannot be misused. |
| Voice | If you have a modem that can detect voice, then PhoneSweep will mark human-answered calls as “voice”. Answering machines and voicemail systems will also qualify as voice. |
6. Appendix: PhoneSweep Audit Report
Dialed Phone Numbers:
| Total Phone Numbers With This Result | Percent of Total Phone Numbers | |
| Assigned to Dial | 88 | 100.0%* |
| Checked for Data | 88 | 100.0%* |
| Carrier | 0 | 0.0% |
| Tone | 0 | 0.0% |
| Busy | 5 | 5.7% |
| Ring Timeout | 27 | 30.7% |
| Timeout | 50 | 56.8% |
| Voice | 0 | 0.0% |
| Screened | 0 | 0.0% |
* As a percent of the total numbers assigned to dial, as opposed to actually dialed.
The percentages may not add to 100 percent and there may be more distinct results than assigned phone numbers. This can happen if a phone number responded in two different ways. Also, if the scan was not completed, the numbers will be less than 100 percent.
Discovered Fax Machines:
| Total Phone Numbers With This Result | Percent of Total Phone Numbers | |
| Assigned to Dial | 88 | 100.0% |
| Checked for Fax | 83 | 94.3% |
| Faxes found: | 6 | 6.8% |
| Screened: | 0 | 0.0% |
Discovered Modems:
| Total Phone Numbers With This Result | Percent of Phone Numbers With Carrier | |
| Numbers with Carrier: | 0 | 0.0% |
| Identified | 0 | 0.0% |
| Unidentified | 0 | 0.0% |
Penetrated Modems:
| Count of systems penetrated | Percent of total penetrated systems | |
| Penetrated Systems | n/a | n/a |
| Identified | n/a | n/a |
| Unidentified | n/a | n/a |
Percent of Brute force username/password guessing attempts completed: 0.0%
Anomalies:
No anomalies were found during this PhoneSweep scan.
Systems Penetrated by PhoneSweep:
PhoneSweep did not succeed in penetrating any systems.
Carrier Numbers Found:
The following numbers responded with a modem carrier, allowing access to that system. This means that an outside person may be able to connect to your network through these numbers.
We recommend that you compare with known modem numbers, and that all modem lines be further checked to be sure that strong security is in place. Examples of poor modem security include (but are not limited to) systems without any passwords or systems with well-known or easily guessed usernames and passwords.
No phone numbers with modems attached were found during this PhoneSweep scan.
Busy Numbers Found:
The following numbers were always busy when called by PhoneSweep. They may be leased lines, or voice or data lines that happened to be busy whenever PhoneSweep checked them. We recommend these numbers be checked further to ensure that they are not unauthorized modems.
733
734
769
801
9 27494289
These always busy telephone numbers can be re-scanned by increasing the Busy Redial value on the Dial Sub-Tab. When this report was generated, Busy Redial was set to 5.
Tone Numbers Found:
The following numbers returned a second dial tone when called by PhoneSweep. These numbers should be closely checked to ensure that outsiders cannot make calls through an internal exchange. If these tone numbers allow long-distance or international calls, you may be a target for expensive telephone fraud.
No second dial tone numbers were found during this PhoneSweep scan.
Fax Numbers Found:
The following numbers responded with a FAX tone when PhoneSweep scanned them. FAX machines do not represent a security risk, although FAX numbers which also responded with Carrier could be unauthorized or misconfigured fax/modems.
707
736
814
9 26644183
9 26671087
9 26671576
Incomplete Scan Areas:
PhoneSweep did not complete scanning for fax machines. Of the 88 phone numbers assigned for PhoneSweep to call, only 83 (94.3%) were actually called.
Identified Systems with Modems:
PhoneSweep did not discover any identifiable modems during this sweep.
Unidentified Carrier Numbers:
PhoneSweep did not discover any modems it could not identify during this sweep.
Responses from Penetrated Systems:
This section suppressed by request.
Responses From Unknown Modems:
PhoneSweep did not receive any response strings from unknown modems.